The expert who wrote the “standards” for password security now admits that he was wrong.
Bill Burr was the technology manager for the US National Institute of Standards and Technology (NIST) when he was asked to create a brief guideline on password security.
His recommendation, which we’ve all become familiar with over the past 15 years, was eight characters mixed with capitals, numbers and “special characters”. He also recommended changing these passwords frequently.
It wasn’t long before this became ubiquitous and every bank, social media platform, and OS took this guideline as rote.
Machines are smart. Humans are ingenious.
While previous attempts at breaking passwords was with “brute-force” — where hackers harnessed sheer computing power to try millions of password combinations until the correct combination is found — Burr didn’t take into account the desire for users to simplify their passwords nor the ingenuity of hackers.
Passwords soon turned into variations of words with numbers and “special characters” substituting their alphabetic brethren:
- A became @
- E became 3
- I became 1
- O became Ø
On it goes until Password1! becomes P@$$wØrd
While, on the surface, the latter seems like a much more secure password (and much more difficult to remember) from the standpoint of “brute-force” attacks, hackers soon learned this new lexicon and added these common substitutions to their dictionaries; thereby undoing any possible increase in password security.
Correct horse battery staple
The solution is to use a long, memorable, passphrase.
The solution is to use a long, memorable, passphrase. Incidentally, the most secure passphrase uses a combination of unexpected words rather than a phrase you’d use in a sentence. The more characters and words that you add, the more difficult they become to crack.
The guideline of changing passwords is also at question as it’s safer to keep a longer, more complex, password than continually change a weaker one.
This is explained particularly well thanks to the infographic designed by XKCD:
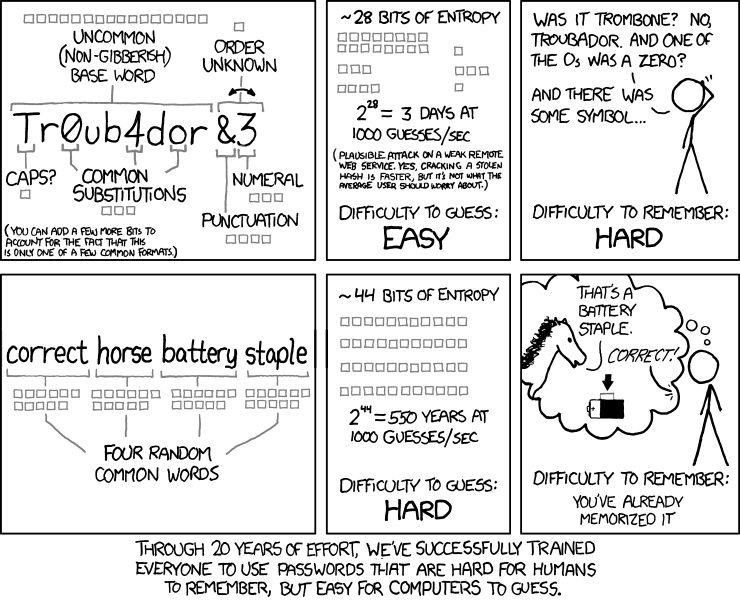
Length does matter
Using four character sets (95 characters including alphanumeric and allowed “special characters”) in an eight character password allow for about 6.634 quadrillion different password possibilities.
Forget all of your passwords
As more and more services move online, the reliance on logins has become even greater.
Unfortunately, repeating the same username and password across a multitude of sites is dangerous as data breaches can and do occur (far too regularly if you ask us). In a world with so many logins and passwords where each site uses a unique password, how do you remember them all?
The simple answer is: you don’t!
The modern approach to password management is to use a password manager that stores all of your passwords in one place, is encrypted, and only makes you remember one password.
If you’re typing in all of your passwords from one location such as your laptop, you can use local password managers that tie into your favourite browser such as KeePass or Enpass.
If, like most of us, you need access to these passwords from various devices such as your phone, laptop, and desktop, then cloud based services such as 1Password, LastPass, and Dashlane have you covered.
Hello, is it me you’re looking for?
Taking security even further, it’s recommended to add another layer of protection by the way of two-factor (2FA) or multi-factor (MFA) authentication.
This is typically offered by many online banks, service providers, and social media sites.
Multi-factor authentication means that one must use two steps to access your information. The first authentication method is your password, the second is a way to prove that you are who you say you are.
This could be entering a code sent to your phone, answering a question that only you’d know the answer to, or using a form of biometric on your phone such as your fingerprint or facial recognition.
Companies like Google, Microsoft, and Apple all offer MFA applications for their devices and third parties such as Yubico and Duo offer additional services or access methods.
Here be dragons
Let’s be clear: there’s no foolproof way of protecting your online accounts, but these are simple methods that will greatly decrease your risks.
As always, be smart about your passwords, don’t reuse the same one over-and-over, and avoid the most common ones.
SplashData has compiled a list of the 2017 most commonly used passwords found in data breaches that you should avoid.
Photo: Mark Burnett on Flickr. Used under CC 2.0 license.

