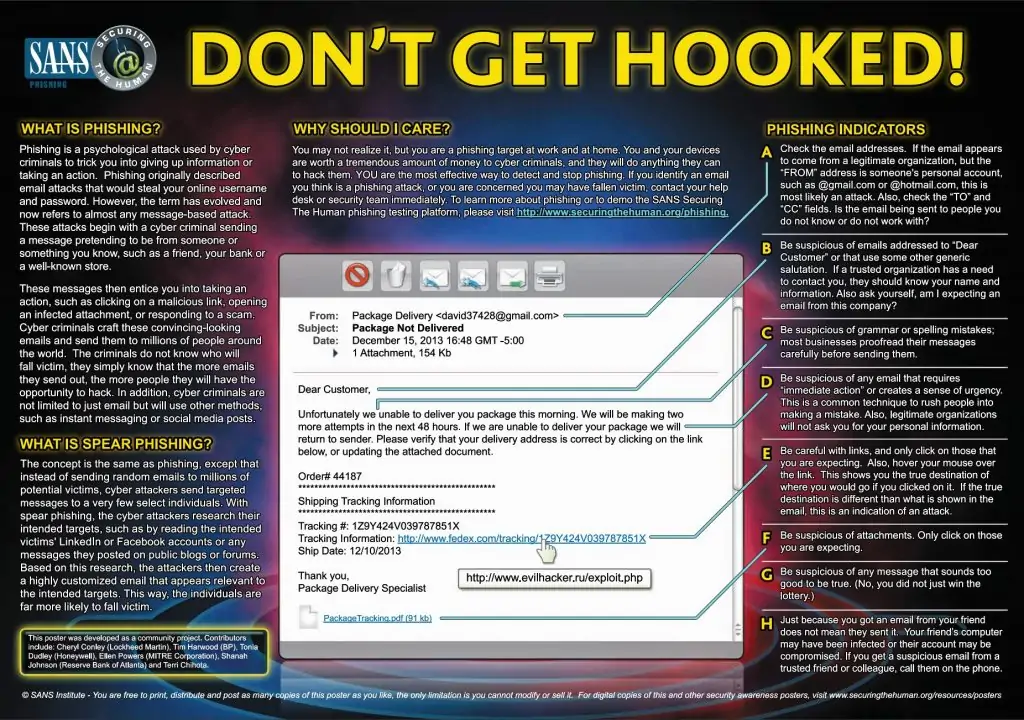
In the last year, phishing attacks have been on the rise as attackers continue to refine their methods and share these findings within their community. Over 90% of cyber-attacks now begin with a phishing campaign.
Phishing is about convincing the user to provide valuable and/or confidential information to the attacker.
While there are several types of phishing campaigns being utilized, the most common are:
- Mass Phishing: These are opportunistic attacks taking advantage of a company’s brand name such as LinkedIn requesting that you update your password, address, or credit card details.
- Spear Phishing: Emails which impersonate a specific trusted sender or source such as your manager. These often request that a document, payment, gift cards, or other information be returned to them via email or to a third-party address posing as a client or vendor.
While many businesses have comprehensive antivirus, no single product will completely protect your business. The user is the last line of defense and “click-happy” end users may inadvertently disclose confidential information, release funds, or download a virus or malware.
As a precaution, we want to remind you to:
- be on the alert for emails that request personal information, even if you recognize the name of the sender. These should always be regarded as suspicious;
- beware of emails requiring your “immediate action” in order to prevent a service from being shut down unless you logon “now” or enter your personal or credit card information;
- before you give out information or take any action that is requested in an email, take a few moments to verify that request, even if the email contains your name and other information that applies to you;
- verify the request using another source, not a source that is provided in the email;
- don’t be fooled by emails that offer “too good to be true” enticements,
- remain wary of unsolicited email and always be cautious in your online activity.
SANS Institute has provided this very helpful poster detailing critical items to look for when attempting to identify an email as valid or fraudulent.